Conference “Cyber Security in Cloud Computing” In light of the great technological development that the world is witnessing, there has become an urgent need to…
Year: 2022
GET TO KNOW WORDPRESS
GET TO KNOW WORDPRESS What is WordPress? WordPress is an open-source content management system (CMS) made in 2003 by Mike Little and Mike Mullenweg in…
Our newest brand has arrived 🎉
Our newest brand has arrived 🎉 In clouds zone we provide everything you need in clouds and technology world with high speed, high quality and…

Cyber Security Tools
Cyper Security Tools 7 tools for examining vulnerabilities and gaps in sites and systems. Since ancient times, mankind has protected itself in several ways to…

24/7 Incident response
24/7 Incident Response Usually when technical problems occur in our business, the first thing we think about is communicating with technical support, and the response…

DDoS Attack – Stressing Attack
DDoS Attack – Stressing Attack In the final stage of the development of any web system that will target users directly, the developers must test…
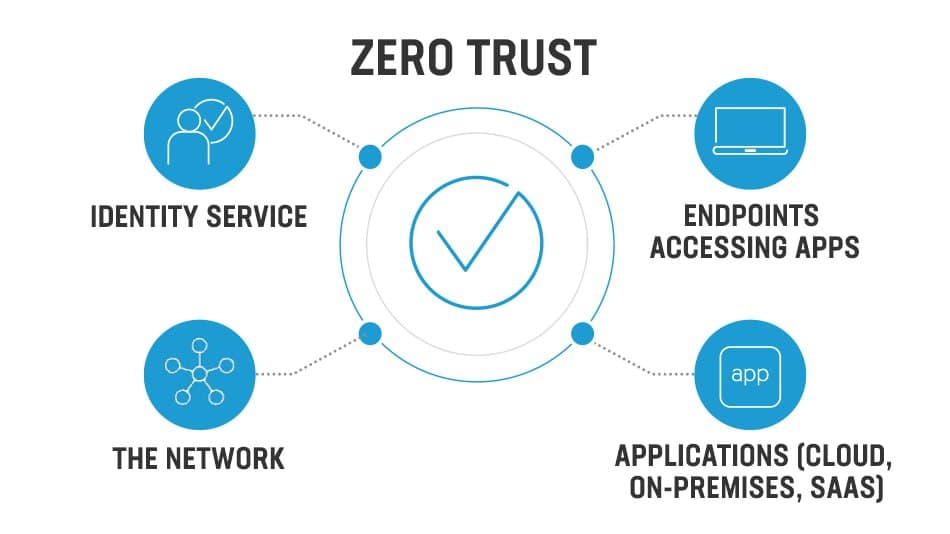
Zero Trust Method
Zero Trust Guiding Principles The Zero Trust model has three principles which guide and underpin how security is implemented. These are: verify explicitly, least privilege…
