Cyper Security Tools 7 tools for examining vulnerabilities and gaps in sites and systems. Since ancient times, mankind has protected itself in several ways to…
Category: Security and Backup

DDoS Attack – Stressing Attack
DDoS Attack – Stressing Attack In the final stage of the development of any web system that will target users directly, the developers must test…
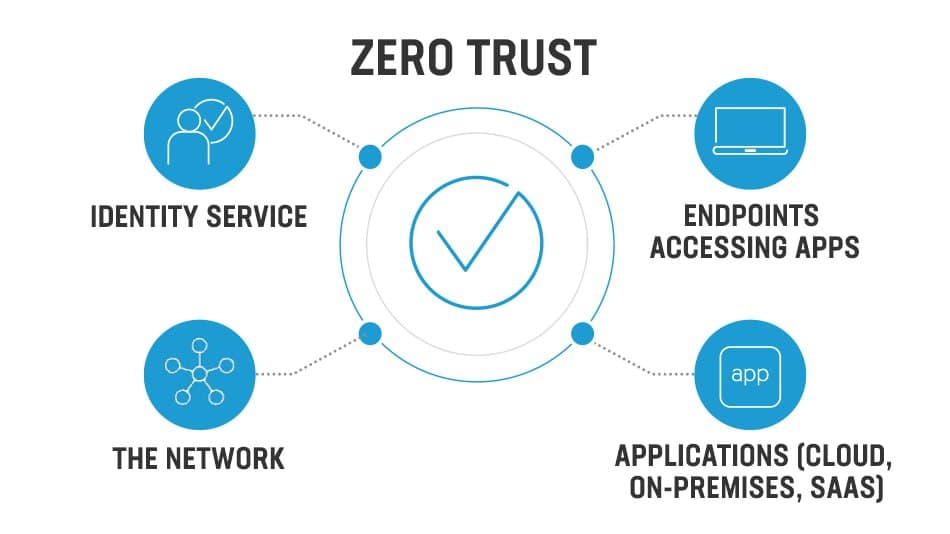
Zero Trust Method
Zero Trust Guiding Principles The Zero Trust model has three principles which guide and underpin how security is implemented. These are: verify explicitly, least privilege…
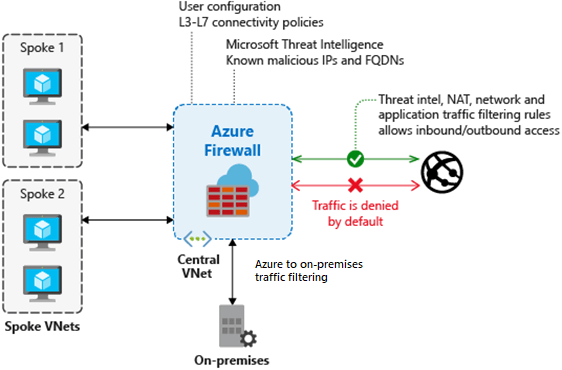
Determine Azure Firewall uses
Determine Azure Firewall uses Azure Firewall is a managed, cloud-based network security service that protects your Azure Virtual Network resources. It’s a fully stateful firewall…

