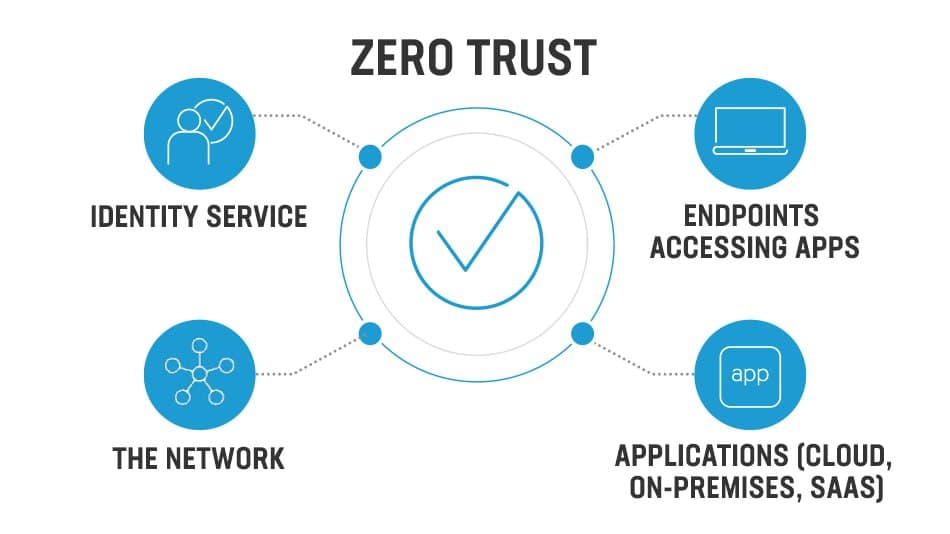
The Zero Trust model has three principles which guide and underpin how security is implemented. These are: verify explicitly, least privilege access, and assume breach.
Verify explicitly. Always authenticate and authorize based on the available data points, including user identity, location, device, service or workload, data classification, and anomalies.
Least privileged access. Limit user access with just-in-time and just-enough access (JIT/JEA), risk-based adaptive policies, and data protection to protect both data and productivity.
Assume breach. Segment access by network, user, devices, and application. Use encryption to protect data, and use analytics to get visibility, detect threats, and improve your security.
In the Zero Trust model, all elements work together to provide end-to-end security. These six elements are the foundational pillars of the Zero Trust model:
We can offer the security audit services by specialized methods and tools to apply well known standards for the SMBs and enterprise companies so with Clouds Zone ITC we can conduct a real cyber attack to evaluate the security grade for your business in global standards by an expert team.
Source: Microsoft Zero Trust
Learn more about Clouds Zone Cyber Services: Cyber Security – Clouds Zone ITC
WhatsApp us
